Looking to store your documents securely?
Try Nanonets. After processing every important business document, you can automatically store your files in our secure storage.
Trusted by 30,000 professionals in 500+ enterprises.
Security has no alternatives, and business documents are no exception.
Documents are your company's assets. They contain sensitive information about the organization, and safeguarding them from fraudulent means is an organization's significant task.
How can you prevent your documents from falling into the wrong hands? : Document Security
Let's look at document security and how you can streamline the process to ensure maximum safety for your documents.
What is document security?
Document security, or document access security, involves safeguarding documents and files from unauthorized access or theft. It encompasses procedures aimed at preventing wrongful manipulation or reproduction of data, ensuring the integrity and confidentiality of sensitive information.
Document security uses different procedures to protect business documents, used internally or externally, by methods like password protection, multi-factor authentication, secure cloud storage, role-based access, and more.
Document security reduces fraudulent access to business documents and ensures compliance.
These are just some ways to ensure you're protecting your documents. But, to be legally compliant, you might have to use a document processing platform like Nanonets, which is SOC2 and GDPR compliant and provides round-the-clock secure cloud hosting for document storage.
Save 80% of your costs with the Nanonets while securing your documents in a GDPR-compliant cloud storage.
Get a free product tour or try it yourself.
What are the different ways to secure documents?
Let's discuss some common ways to secure documents. Some people like to use more than one method simultaneously to improve their document security.
Now, when you're looking to secure documents or you're searching for your next document security platform, look for these most common document security elements listed below:
- Role-based restricted access
- Document encryption
- Adding watermark
- Adding passwords to documents
- Document expiry
- Document tracking
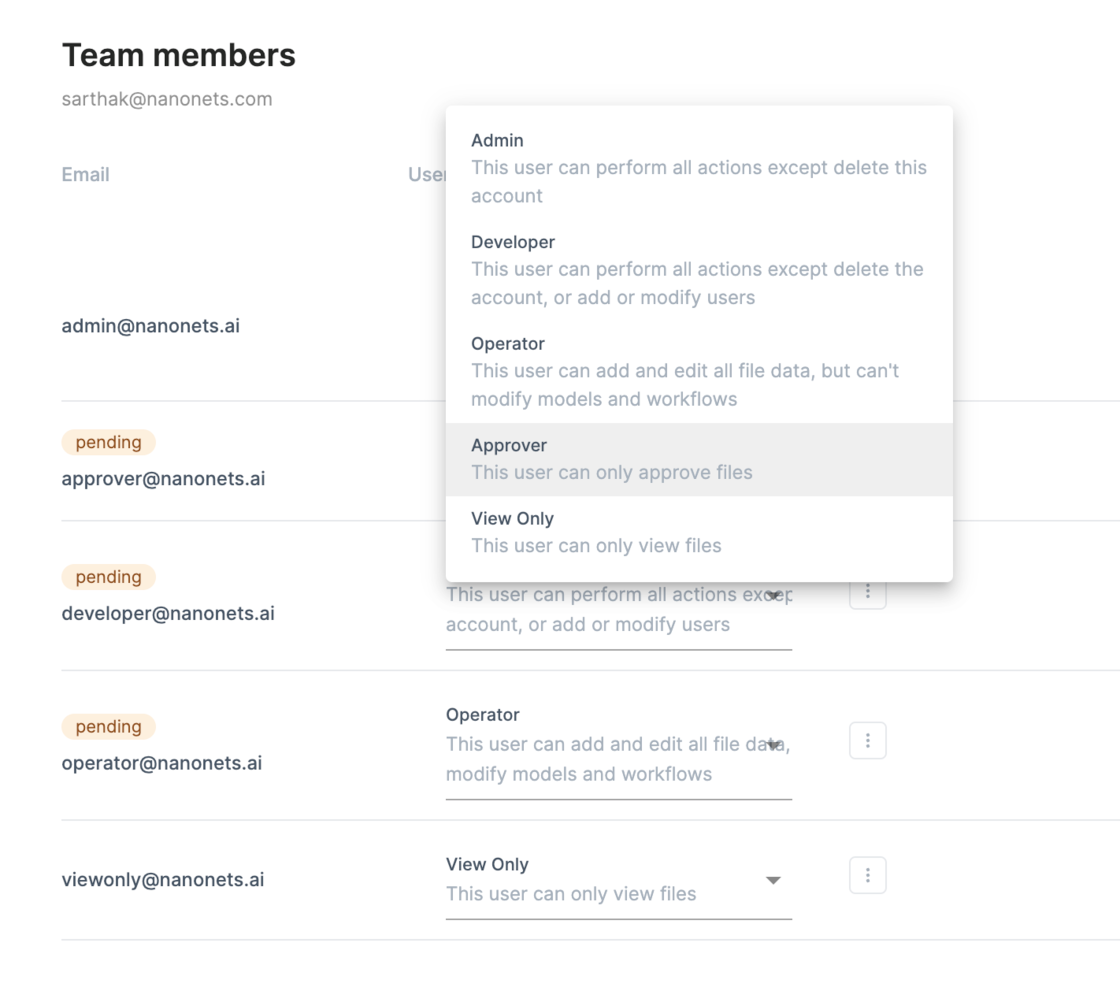
Role-based restricted access
One of the simplest ways is to restrict document access. The fewer people see it; the fewer people use it.
On most document security platforms, you can restrict access to limit the number of users accessing the documents. Administrators can keep track of the t
Document Encryption
Document encryption encrypts documents so that only the people with the associated cryptographic key can see what's inside the document. There is no way to decrypt the file without the right key, even if it ends up in the wrong hands.
Documents can be sent or stored with encryption applied to them. This is a great way to secure documents.
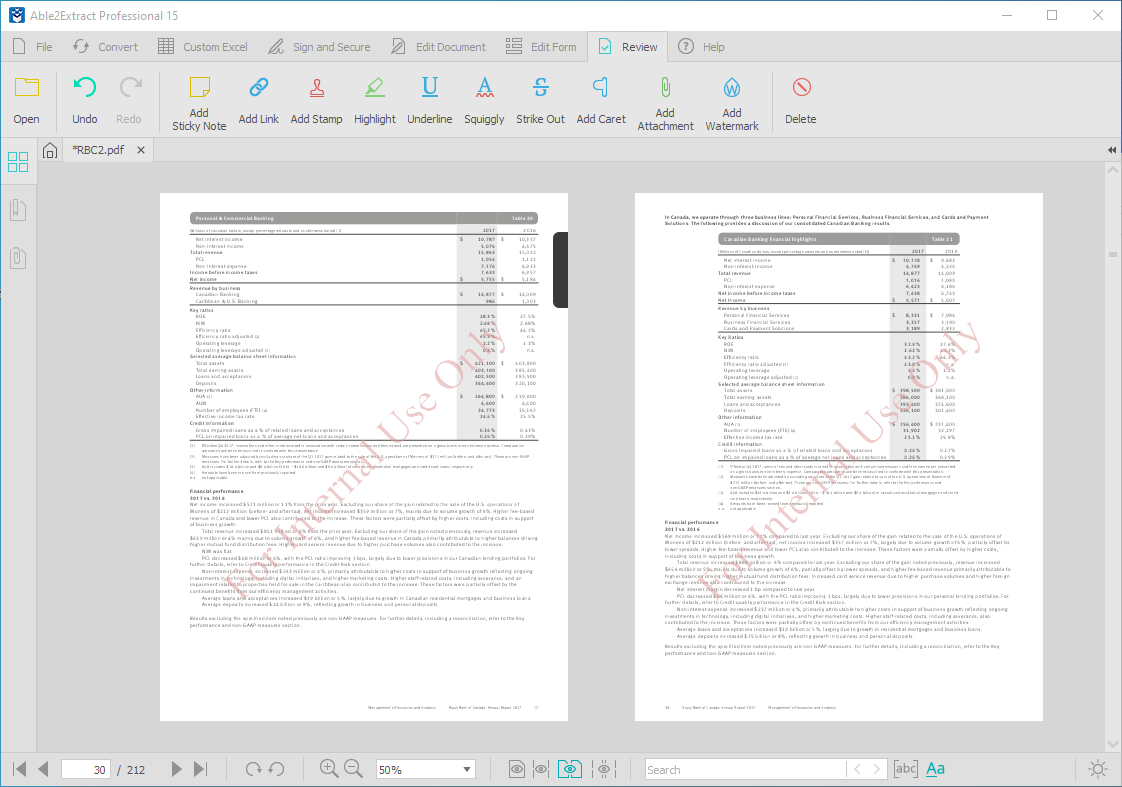
Adding a watermark
Adding a watermark is a great way to show the real source of documents. Watermarks are used in video content to trace the content back to the creator. Adding watermarks to documents in the form of text or content can notify users that the material is private. This serves as an additional warning to be cautious about where and how the document is shared.
Adding passwords to documents
Enabling password protection is the simplest way to secure documents. Without the password, the document can't be accessed if, for whatever reason, it ends up in the wrong hands.
Of course, you need a safe method for storing, sharing, and changing passwords. You might put it on a secure server that only authorized individuals can access.
Document Expiry
It's good document security hygiene to delete old documents regularly.
Employing document expiry policies may ensure that information doesn't stay around any longer than it needs to. You can set up automated workflows to check documents that are maybe three years old (and not required by tax or government), delete duplicates, and manage downloads or multiple document versions.
Document tracking
Document tracking lets you know who downloaded, printed, and read the document. The locations, IP addresses, and frequency of user access to the asset may be visible to you, depending on the document security option you choose.
Enhance document security with GDPR-compliant cloud storage, role-based access, automated document workflows, and more.
Save 90% time & 80% cost with Nanonets. Book a 10 min call to see how.
Try Nanonets for free, or book a call with our automation expert!
Why is Document Security Important?
Document security ensures that an organization's sensitive information is safe and secure across all communication channels. But is it that important? It turns out it is. Document security is important because it:
- Builds customer trust in your services: A company that doesn't protect customer data or documents will always face the consequences.
- Lowers financial consequences of a data breach: In case of data breach, companies have to shell out almost $4.5M! That's a huge amount.
- Reduce the risk of document corruption: When you store data in damaged hard drives or insecure cloud storage, hackers can use the opportunity to install malicious software.
Document security is not optional but a necessity in case of compliance. Eevry company is required to prove their secure document processes to be granted GDPR or SOC2 compliance which plays an important role in bagging clients.
Secure your business documents with Nanonets.
Trusted by 30,000+ users from 500+ enterprises. Rated 4.9 on G2. Give it a try!
Start your free trial or schedule a call with us.
How to improve document security?
You can improve document security using an automated document management system like Nanonets.
Nanonets have multiple features that help organizations improve document security.
Digitize Paper Documents
Digital documents are easy to manage. Nanonets can convert your paper documents into electronic records, leading to easy document management.

Secure Cloud Storage
Nanonets is a SOC2 and GDPR-compliant intelligent document processing platform that provides free document storage to all clients.
Automated document tracking
Nanonets can extract metadata from documents, keep track of document metrics, provide role-based access, monitor document changes, and show where documents are stored easily.
Nanonets can track who accessed which documents and when and what changes were made. This is extremely helpful if you need to know who read, shared, and worked on the document.
Apart from these, Nanonets gives you complete visibility into all your document processes and automates manual processes like approval, document access, and document audit trail so you can focus on essential tasks.
Why should you use Nanonets?
- 14 day free trial
- Setup in 1 day
- Easy to use
- SOC2 and GDPR compliant
- Free cloud document storage for every customer
- Cloud & On-premise hosting
- Powerful OCR software
- End-to-end document processing workflows
- 24x7 support
- Free migration assistance
- Free consultation call with automation experts
- 10,000+ satisfied customers
- 30Mn+ documents processed yearly

Book a 10-minute call, and we'll review your current document processes or help you optimize your document processes with no-code workflows!
Tips to Improve Document Security
Unstructured data, unsafe files, security breaches, human errors, and illegal storage access are key issues with document security. You risk losing customer information, financial information, and even ongoing business relationships. Although document security is a complex subject, the following tips can help you improve document security:
Tip 1: Use a good document management system
A document management system will help you implement many document security measures at scale and on autopilot. Some of these measures include role-based access, password protection, audit trails, document digitization and more.
Also, the majority of service providers provide secure cloud storage which reduces the risk of insecure document storage.
Tip 2: Be conscious of shared devices.
Another vulnerability in document security is shared equipment like printers. Only authorized customers should be permitted access to the systems' resources and network applications to reduce the hazard.
Protect hardware with password authentication & keep a complete audit trail of every document activity from these devices. To stop someone from stealing your confidential data or infecting your company's network, access to physical ports is frequently blocked as a standard security measure.
Tip 3: Educate employees on phishing
Today, most successful cyberattacks originate from phishing emails. Educate your employees to check
- the sender's actual email address first, not just the sender's name, so to speak.
- typos, inaccurate or marginally modified logos should also catch your eye.
- double-check the email with your IT staff if they have any doubts.
Tip 4: Use passwords effectively
Attackers will find it more challenging with a strong password policy and Multi-Factor Authentication. Here are a few fundamental guidelines regarding passwords:
- Never keep your passwords written anywhere
- The better, longer, and more complicated the password, the better.
- Use a unique password only once across all of your accounts and platforms.
Conclusion
For all businesses, maintaining high levels of document security is essential. Without it, competitors might be able to gain private information about clients or employees might have access to compensation or performance information that they should not. The danger of exposing sensitive information to the public can be significantly decreased by using organization-wide document management and document security best practices.
Nanonets help businesses optimize their document processes with no-code workflows in 15 minutes. Contact us for a free demo where our automation experts will guide you on how you can use Nanonets to manage documents like a pro! You can also use Nanonets' as a white-label document management system.
Read more:
- Find the best document management software
- 10 Best Document Automation Software
- How to automate document verification?
- Verify 10,000+ ID cards with automated ID verification
- How to archive documents properly?
- Which are the best legal document management software?
- How to classify documents using document workflows?
- Enhance document security with Nanonets
- Automate document indexing with no-code workflows
- The 2023 Guide to Document Automation
- Top EDMS systems in 2023
- The 2023 guide to document processing
FAQs
What happens if you don’t protect your documents?
Here are a few examples of the negative consequences of losing documents:
Competitors gain access to private information, such as the profit of the company or employee records. The workers gain access to data like promotion updates beforehand. Security breaches rise due to the theft of data. Moreover, hackers can gain access to sensitive data. Teams in the corporation become less productive due to the theft of correct data, which can lead to clients losing trust in the company.
What are the advantages of document security?
It may seem impossible to tackle the process of digitizing vast amounts of documents. But organizations who decide to invest in an electronic document management system provide themselves the groundwork to help automate workflows and expand mission-critical procedures. Given below are the main advantages of setting up an electronic document management system for your company and increasing business productivity.
- Increased productivity
- Better collaboration
- Reduced Storage Space
- Enhanced security
- Improved Regulatory Compliance
- Easier Document Retrieval
- Better Backup
How do you ensure the security of documents?
You and your staff view an electronic document via PCs and mobile devices. They employ passcodes to accomplish it. To prevent your staff from disclosing their location when accessing the web, make sure you set up a VPN on any device. You can disable any device's automatic password remembering. You should instruct everyone to follow suit when conducting employee training. Sensitive information could be made public if the lost gadget recalls all of the passwords to the company's assets.
Also, ensure that you do not let your staff members use their personal devices to store private information. You can achieve this by turning off the export of electronic documents.
What is the major component of document security?
There are many different techniques and disciplines that makeup document security. It seeks to protect your data from illegal access and maintain its integrity, prevent malware from taking hold of your devices and networks, store the crucial data for when you need it, enable a secure and seamless information transfer between networks and devices, and safeguard your networks.
Document security measures are compartmentalized to ensure that all potential risks are addressed due to varied and complex responsibilities of document security protocols. Confidentiality, integrity, and availability—aspects of the document's security—are the components that specify its accountability.
Confidentiality
Confidentiality is the act of concealing. It indicates that only authorized individuals can see the material. The first step in document security is to prevent the document from being viewed by unauthorized people.
Integrity
Integrity implies originality, and this component is used to ensure that the data is accurate and undamaged. Ensuring that the document isn't changed due to an error or a criminal act is part of maintaining integrity.
Availability
A relatively simple concept of document security is the document's availability. The phrase means having ready access to the data. The relevance of availability is increased by hostile attacks that try to prevent authorized users from accessing the data.
What is digital document security?
One of the main objectives of organizations nowadays is protecting digital documents that hold vital information and data. A data breach can have many negative effects that go beyond the simple loss of important information. A data breach may have negative financial effects, reputational harm, and potential legal ramifications.
Because they include a variety of vital information regarding both personal and organizational data, digital documents are objects that need to be secured. Securing digital documents, which also refers to securing information, ensures business continuity, lowers risk, and maximizes return on investment.
Your digital papers can be protected using encryption. A document is encoded through the process of encryption so that only those with the necessary access can open and decrypt it. Users must need a password or pin code to decrypt encrypted data. Encryption is a crucial yet straightforward procedure to ensure that your digital documents are safe while being kept and transported.
Use Nanonets to automate the document storage process & organize your files on autopilot!